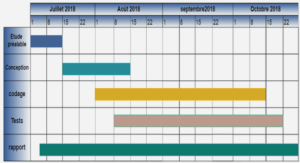
WIRELESS AD HOC NETWORK BACKGROUND
Wireless Ad Hoc Networks
A wireless ad hoc network is a network deployed without any pre-existing infrastructure, which can be built on dynamically without any centralized administration (see Figure 1.1). The lack of a central authority and predefined infrastructure require all nodes in the network to participate actively in the common network functions, such as routing, addressing, security, etc. Nodes are free to move arbitrarily in the network, breaking and creating links dynamically, thereby constantly changing the topology of the underlying network.
The nodes participating in an ad hoc network must handle the routing process without the support or supervision of a central authority or any previously established infrastructure. As those nodes usually have a limited range of transmission, the packets exchanged between two nodes that are outside each other’s transmission range must be forwarded on a hop-by-hop basis by intermediate nodes until the destination is reached. Due to their self-organization and rapid deployment capabilities, mobile ad hoc networks can be used for several purposes, for example in battlefield communications, sensor networks, emergency relief scenarios, public social services, the virtual class room, etc.
Mobile Ad Hoc Routing Protocols
Unlike classical wired and wireless infrastructure networks, where packets are routed toward a destination using central authority devices (e.g. base stations or routers) and a predefined infrastructure, in ad hoc networks, the functions performed by those elements must be achieved by the nodes themselves. The inherent characteristics of ad hoc networks, such as its high mobility, fast topology changes, and battery power limitations, have made the routing protocols used in traditional networks inaccurate.
This means that other routing protocols specially designed for ad hoc networks must be used. Based on the route created, ad hoc routing protocols can be classified into two main categories: (a) proactive; and (b) reactive. In a proactive routing protocol, the nodes register the changes in the network topology and periodically update routing information. In contrast, in a reactive routing protocol, the routes are discovered on-demand, i.e.only when they are required.
Solutions for closed (Layer-2) wormhole attacks
As mentioned in section 2.1.2, closed wormhole attacks are developed by external agents seeking to threaten the security of the network by attacking the neighbor discovery (ND) protocol. The nature of wireless ad hoc networks, where the mobility of the nodes generates a constant modification of the network topology, makes attacks against ND relatively easy and securing ND a difficult problem (Poturalski, Papadimitratos and Hubaux, 2008).
In the closed wormhole attack, an external attacker falsely convinces a group of honest nodes that they are neighbors. The proposed solutions to thwart this attack are based on the deployment of a secure neighbor discovery protocol which allows an honest node to verify that the distance separating it from a remote node is shorter than the maximum allowed transmission distance in the network. The solutions proposed for securing the ND protocol can be organized in several groups, according to their characteristics.
|
Table des matières
INTRODUCTION
CHAPTER 1 WIRELESS AD HOC NETWORK BACKGROUND
1.1 Wireless Ad Hoc Networks
1.2 Mobile Ad Hoc Routing Protocols
1.2.1 Proactive Routing Protocols
1.2.2 Reactive Routing Protocols
1.3 Major Routing Protocol Attacks in Ad Hoc Networks
1.3.1 Black Hole Attack
1.3.2 Spoofing Attack
1.3.3 Sybil Attack.
1.3.4 Wormhole Attack
CHAPTER 2 WORMHOLE ATTACK
2.1 Classification of wormhole attacks
2.1.1 Classification of wormhole attacks based on communication techniques
2.1.2 Classification of wormhole attacks based on the visibility of malicious nodes
2.1.3 Active-x-y wormhole attack model
2.1.4 OSI Layer wormhole attack model
2.1.5 Conclusion
CHAPTER 3 REVIEW AND ANALYSIS OF WORMHOLE ATTACK COUNTERMEASURES
3.1 Solutions for closed (Layer-2) wormhole attacks
3.1.1 Distance Bounding solutions
3.1.2 Location-aware approaches
3.1.3 Graphical and statistical techniques
3.2 Solutions for open (Layer-3) wormhole attacks
3.2.1 Location-aware approaches
3.2.2 Statistical technique
3.2.3 LiteWorp and MobiWorp
3.2.4 Trust-based solutions
3.2.5 Network visualization
3.3 General summary of existing wormhole attack solutions
CHAPTER 4 WIM-DSR
4.1 Multipath Source Routing
4.2 Strong and Weak Open Wormholes
4.3 Assumptions and Treat Model
4.4 Edge Witnesses
4.5 WIM-DSR Route Discovery
4.6 Analysis
CHAPTER 5 SIMULATION RESULTS
CONCLUSION
BIBLIOGRAPHY
![]() Télécharger le rapport complet
Télécharger le rapport complet